There are some advanced solutions to protect and mitigate our infrastructure against DDoS (denial of service attacks). Today, we are going to delve into them.
Before getting into the matter, we have to be aware of where we are with regard to denial of service attacks.
The growth of denial of service attacks has increased exponentially in the last 5 years, not only in the number of attacks, but also in the volume and bandwidth that these attacks consume, affecting companies that seemed impossible to attack due to their large investment in security and the size of its infrastructure (most serious cyber attack in the last 10 years).
We are ending the year 2020, where there has been an increase of more than 80% in the number of denial of service attacks.
In the last month, the volumetric attack with the highest capacity in history has been registered, reaching 1.7 Tbps. The predictions for the next few years are not encouraging, some media predict that they will multiply by 100 in 2021 and the rise will be exponential in the following years.
We are reaching a point where hiring or implementing these attacks is too cheap and the damage they can cause to the competition generates very high costs.
It is estimated, that the cost of a DDoS attack on small and medium-sized companies causes, on average, losses of $ 120,000 and in large companies about $ 2,000,000, and this is something that in the current situation, with thousands of people teleworking (digitization of services and companies), it will increase and may make companies have to assume these losses or be forced to make a strong investment in security.
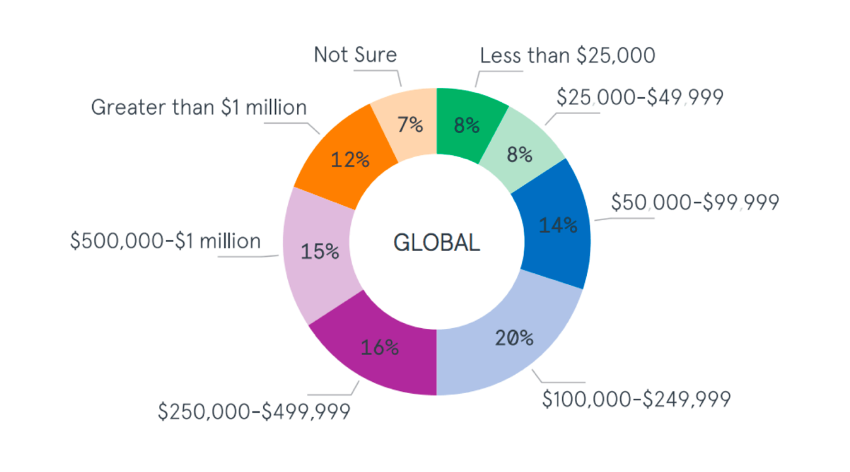
Cost of DDoS attacks on SMEs
DDoS mitigation
We are going to divide DDoS mitigation techniques into several phases, to understand what possibilities we have to defend ourselves against DDoS attacks on any infrastructure.
DDoS prevention
One of the basic priorities that we have and that we can call phase 0, is the prevention of attacks. This requires a series of measures that will make it very difficult for us to attack from programmed botnets and very basic attacks.
It must be taken into account that in cybersecurity there is the concept of “hacking value”, which is the relationship between the difficulty to attack and the benefit that can be obtained. If the target is very easy to attack, the “hack value” increases; on the contrary, if an organization of cybercriminals wants to attack us and they do not see an easy attack surface to exploit, they are likely to seek another target.
Measures that can be taken:
- Improve network architecture. It is important to have several security zones, in which we increase protection, as we expose ourselves to the Internet. DMZs are areas that are relatively isolated from internal resources, providing a high level of security and with a “front-end” and “back-end” architecture. This means that the servers that are publicly addressed on the Internet do not contain user data or sensitive information.
- Higher performance and bandwidth. The oversizing of resources will help us in the event that we receive a volumetric DDoS attack. The greater capacity our infrastructure has, the more difficult it will be to get a denial of service.
- L7 Firewall. Something quite basic currently, is able to filter and create robust policies based on applications, where we will only allow access to the applications that are used, checking L7 parameters. Layer 3 and 4 filtering is no longer effective as there are many packet evasion and obfuscation techniques.
- IPS / IDS. It is common that the equipment that we have in an infrastructure is not 100% updated and protected. An IDS / IPS engine will help us protect from existing vulnerabilities and warn us in the early stages of an attack such as recognition, scanning….
- Hardening. It must be engraved on the head that all the computers that make up a converged network must be robust computers, and that only allow the entry of traffic to legitimate services. Many attacks are carried out on protocols such as DNS, NTP and UDP; These protocols must be kept only, if they are strictly necessary from the Internet to our network (Server) and if they are used, secure them as much as possible.
DDoS detection
If we receive a DDoS attack, we must have the ability to detect and differentiate them from legitimate traffic. The detection phase is essential to be able to take action on the different traffic that enters our network. There are many very reliable detection methods, of which we get very few false positives. The most advanced DDoS attacks use legitimate traffic and spoofing techniques to make it appear that the traffic we are receiving is legitimate.
Detection methods have become a challenge for all security vendors. DDoS attacks have evolved in recent years, with attacks that are very difficult to detect and differentiate from legitimate traffic. Depending on the type of business we have and the criticality of the services, we must have more basic or advanced detection methods to be able to filter the “dirty” traffic and that the applications can continue to function under a DDoS attack. In another article, we will detail the forms of detection, since there are many of diversity and complexity.
Responding to DDoS
After detecting illegitimate traffic, we must apply different actions and responses to be able to prevent this traffic from reaching our communications infrastructure.
- Re-routing. It consists of re-“routing” prefixes in smaller portions by different ASs. Not all companies have AS (autonomous system) and the ability to do this over BGP. External services can be hired for re-routing.
- Black Hole Routing. When we detect a DDoS attack to an IP or from an IP it is added to a black hole or a route to null, that is, a route to a bit bucket, and therefore we prevent malicious traffic from entering our network.
- SinKHoling. A database is used with malicious IPs that are blocked or sent to a non-existent destination. It is not a very effective technique since the latest DDoS attacks use thousands of different IPs.
- Scrubbing Center. It is a filtering center prepared with advanced technology to absorb all incoming traffic and using different detection and filtering techniques (SYN proxy, thresholds, HTTP cookie, L7 inspection…), which only allows legitimate traffic to enter the network. Traffic must be diverted to a scrubbing center and this will return only clean traffic.
Adaptation after DDoS
The last step is to analyze and have a response plan for denial of service attacks. Once we have suffered DDoS attacks it is important to trace these attacks, analyze the techniques that have been used and improve the security and communications infrastructure.
It is a “living” process, where it is essential to have qualified professionals with the necessary experience to make decisions that improve security against DDoS, without affecting the functionality of applications and services.
You can see our Cybersecurity Solutions

